As organizations increasingly move data and services to Azure, it can be difficult to assess whether the services are implemented in a secure fashion. Many of the traditional datacenter security good practices apply in Azure, but they don’t necessarily translate in an obvious way. Moreover, with the ease with which an administrator can add resources, it’s difficult to keep track of where the vulnerable endpoints are. It uses advanced analytics, including machine learning, and Microsoft’s vast global threat intelligence, to detect more than 140,000 threats per month!
The Azure Security Center Landing Page in our lab – VMs need patching and there’s a lot of exposed RDP, which is why it’s all red.
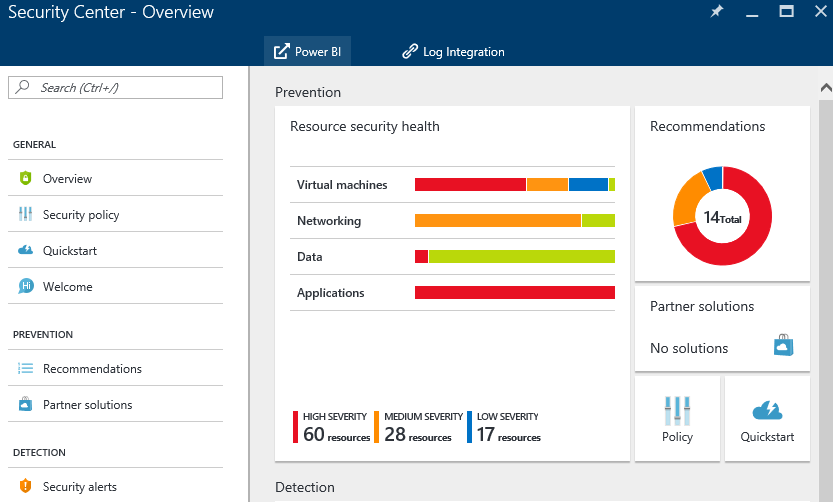
Azure Security Center’s free tier helps administrators assess their security posture by scanning for commonly overlooked configurations, such as unsecured public IPs, web applications without a WAF, and subnets without security rules. Detections often have a quick “one click” action that administrators can take to remediate the issue, or some quick documentation of the subject. In the example below, clicking one of the listed VMs brings up a prompt to select an existing WAF (if you have one) or create a new one in your environment.
The Standard tier adds a lot more detection capabilities, including assessing VMs for vulnerabilities and (recently announced) threat detections, such as outbound DDoS and odd RDP behaviour. The true power is really realized in the behavioural and anomaly analytics that are applied. In our lab, for example, it flagged 92 simultaneous incoming RDP connections to one server as being “abnormal for the environment”. The full detection capabilities are documented here, and are continuously being improved and evolved. For most of the Standard tier detection, an agent must be installed on the VM (and therefore, only certain operating systems are supported – but there’s decent Linux support already) which collects information from logs and some other sources within the VM, and exports it to an Azure Storage Account for each region.
You’re able to set up prevention policies, depending on what you determine to be a risk in your environment (for example, a WAF may not be required for some VMs that listen on port 443, or a WAF may be already in place, just not detected by Security Center).

Prevention Policy
What’s really useful about this service is that organizations effectively have Azure’s security team pushing alerts to their operations team on a regular basis. Odd behaviour – even odd specifically for the environment – is detected and an alert is created. As threats change, the Security Center team updates the threat detection. This kind of operation, if an organization were to sponsor and set it up themselves, would be quite expensive, and finding good people to run it is difficult, if reports on ZDNet are to be trusted.
You are able to export the logs from Azure Security Center to a SIEM of your choice, which, along with Azure’s rich logging for service diagnostics, platform audit logs, and your application’s logs can help defenders track and analyze attacks against your systems in the cloud.
Security Center is a great place to get started in securing your infrastructure, and you may learn something to apply to your on-premises infrastructure as well. At the Free tier, it catches misconfigurations, and at the Standard tier, it performs as a pretty decent automated SOC. I recommend that all my clients turn on the Free Tier, and assess the Standard tier. Get started with the Operations Guide here.

